Evaluation Guide
Mar 14 2025
Server General Inc
0. Introduction
This document is a primer for organizations evaluating Transfer General™'s secure data migration SaaS platform across cloud providers and data centers. It covers the installation and testing of the Transfer General Console™ (TG Console) and Transfer General Nodes™ (TG Nodes) demonstrating secure encrypted data transfers.
The guide assumes familiarity with deploying and configuring Ubuntu 22.04 (64 bit) servers and root access. It does not include detailed instructions for installing/provisioning underlying servers.
1. Background (Transfer General™)
Transfer General™ (TG) is a secure and high-speed data-migration platform designed to transfer sensitive data between cloud providers and/or data centers under regulatory compliance, e.g., FedRAMP. The system consists of two main components:
- Transfer General Console™ (TG Console): A web-based management dashboard that provides centralized control over the Transfer General™ system. Administrators use TG Console to initialize the system, manage TG Nodes, oversee data transfers, and rotate encryption keys.
- Transfer General Nodes™ (TG Nodes): TG Nodes handle data encryption, decryption, access control, logging, and data transfer. Each node can both send and receive data, enabling flexible migration paths between connected locations. TG Nodes are deployed on cloud providers and/or data centers to move data to and from their physical locations
Key Features:
- Data Encryption: TG encrypts all data at rest using strong cryptographic algorithms ensuring that said data remains secure at all times from ingestion to migration, i.e., the entire life cycle of any data migration is always secure.
- High-Speed Data Transfer: By leveraging private connections among TG Nodes, Transfer General™ can transfer encrypted data at speeds of up to 50 Gbps, making it suitable for large-scale migrations.
- Versatile Cloud Platform Support: Transfer General™ enables secure data migration between cloud platforms, AWS, Azure, Google Cloud Platform, and others–including on-premise data centers.
- Centralized Management: The TG Console offers a unified interface for administering all aspects of the Transfer General™ system, including node deployment, key management, and transfer operations.
- Data Encryption Key Control: Organizations maintain full control over their data encryption keys through the Security Officer and Data Administrator roles, ensuring the keys remain under the organization's authority and are never exposed to unauthorized entities throughout the migration.
2. Requirements
TG Console Prerequisites:
- A machine or VM to host TG Console
- A modern web browser
- Network access to TG Nodes
- Unrestricted outbound access to the Internet
- A valid license. If you do not have a license you can get a trial license during configuration.
TG Node Prerequisites:
- A valid or trial license. A trial license can be obtained from https://www.servergeneral.com/get-license
- Ubuntu 22.04 servers deployed at source and destination locations.
- SSH access between TG Console and TG Nodes.
- Unrestricted outbound access to the Internet.
Additional Equipment
For TG Node installation and configuration:
- Network connection that is 300MBps or faster between nodes. A slower connection will result in slower data transfer speeds.
- SFTP client for data ingestion and extraction (e.g., WinSCP for Windows users)
- Administrative access to the deployment environment
Network Connectivity
TG Console and all TG Nodes must be able to connect to our licensing server and key lockers within the Server General network. No special network configuration is needed as long as the components have outbound access to the Internet for the ports outlined below.
Before you start, verify that:
- TCP 443 (HTTPS) is open for outbound connections
- TCP port 22 (SSH) is accessible between TG Nodes that will communicate with each other and TG Console
Personnel
The Transfer General™ framework requires two main roles and their associated keys:
- Server General Admin (sgadmin)
- The SG administrator responsible for managing TG Console and TG Nodes
- Used as login credentials for TG Console web access
- Security Officer (SO)
- Responsible for system security and Data Administrators
- Uses the Security Officer Master Key (SMK)--a passphrase for security administration
- Data Administrator (DA)
- Responsible for transfer operations and sensitive data sets
- Controls vault operations and data transfers between nodes
- Uses the Data Administrator Master Key (DMK)--a passphrase for vault access and data encryption
For evaluation purposes, a single person may occupy these roles.
Key Terminology
- Vault
- Encrypted storage within TG Node
- Must be opened to access clear-text view of encrypted data
- Automatically closes during transfers for data integrity
- Uploader
- SFTP user for uploading data to source node
- Uses
/home/uploader/uploaddirectory - Accessible when vault is open
- Downloader
- SFTP user for retrieving data from destination node
- Uses
/home/downloader/downloaddirectory - Accessible when vault is open
3. Evaluation/Test Configuration
To evaluate Transfer General™, you will need the following:
- TG Console
a. One Ubuntu 22.04 server
b. Deployed on your local machine or a dedicated server
c. Network connectivity to all TG Nodes
d. One system user (sgadmin) with root access
e. Web browser access - Source TG Node
a. One Ubuntu 22.04 server
b. Connectivity to the Internet
c. Network access to the data source - Destination TG Node
a. One Ubuntu 22.04 server
b. Connectivity to the Internet
c. Network access to the target storage location
4. Testing Goals and Suggestions
The following are key capabilities to evaluate in the Transfer General™ system:
- TG Console Management:
- Verify UI navigation and responsiveness
- Test node deployment and configuration
- Manage encrypted data transfer operations
- Assess system monitoring and reporting features
- Security Features:
- Validate data encryption at rest
- Enforce role-based access control
- Mange key creation and rotation
- Test vault operations (open/close)
- Data Transfer Capabilities:
- Validate a point-to-point network for secure data traffic
- Measure node-to-node encrypted data transfer speeds
- Confirm data integrity through checksums
- Review data logs
- Integration Features:
- Test SFTP/SCP functionality
- Network share (NFS and SMB) compatibility (coming soon)
5. Deployment Assumptions
- A machine or server ready to host TG Console
- Two valid Transfer General™ 30-day trial licenses for your TG Nodes
- A trial license for TG Console can be obtained during first time setup in the app
- Two Ubuntu 22.04 hosts at your source and destination locations for TG Nodes
- One Ubuntu 22.04 host for TG Console
- Root access on all servers
- Network connectivity between all components (TG Console and TG Nodes)
6. Transfer General™ Threat Model for Data Migration
The following table outlines the threat model for Transfer General™ and its mitigation strategies:
| Actor | Threat | Mitigation by Transfer General™ |
|---|---|---|
| External Attacker | Man-in-the-Middle (MITM) Attack | - Data is encrypted at rest within TG Nodes - Secure node-to-node communication - Strong cryptographic algorithms for data protection - Private, authenticated connections between nodes |
| Insider | Unauthorized Data Access | - Role-based access control - Separation of Security Officer and Data Administrator roles - Detailed audit logging of all operations - Vault-based data protection |
| System Administrator | Privilege Escalation | - Strict separation of system and data management roles - Encrypted data vaults inaccessible to system administrators - Key management controlled by Security Officer |
| Network Provider | Data Interception | - End-to-end encryption between nodes - Secure key exchange protocols - No cleartext data transmission |
7. TG Console Deployment
Let's begin with deploying TG Console, which will serve as your central management interface for the Transfer General™ system.
Step 1: Installation
The user "sgadmin" is a regular Unix/Linux user. Steps to install Transfer General is the are the following:
wget https://www.servergeneral.com/tg-installchmod +x tg-installsudo ./tg-install
Step 2: Initial Access
- Open a web browser and navigate to the TG Console URL (https://<address of your server>/new)
- You may see a warning about the SSL certificate - this is expected for evaluation setups
- Click "Advanced" and proceed to the TG Console interface
- Log in using the "sgadmin" credentials you configured during installation
- Log in using:
- Username: sgadmin
- Password: (configured during installation)
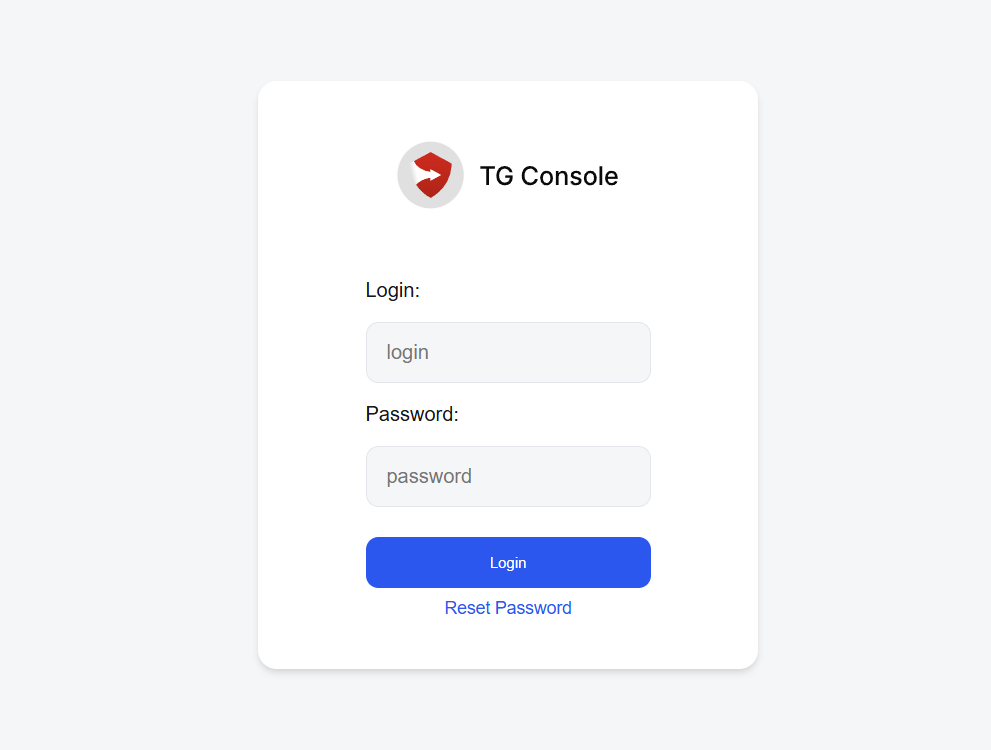
- Accept the license agreement
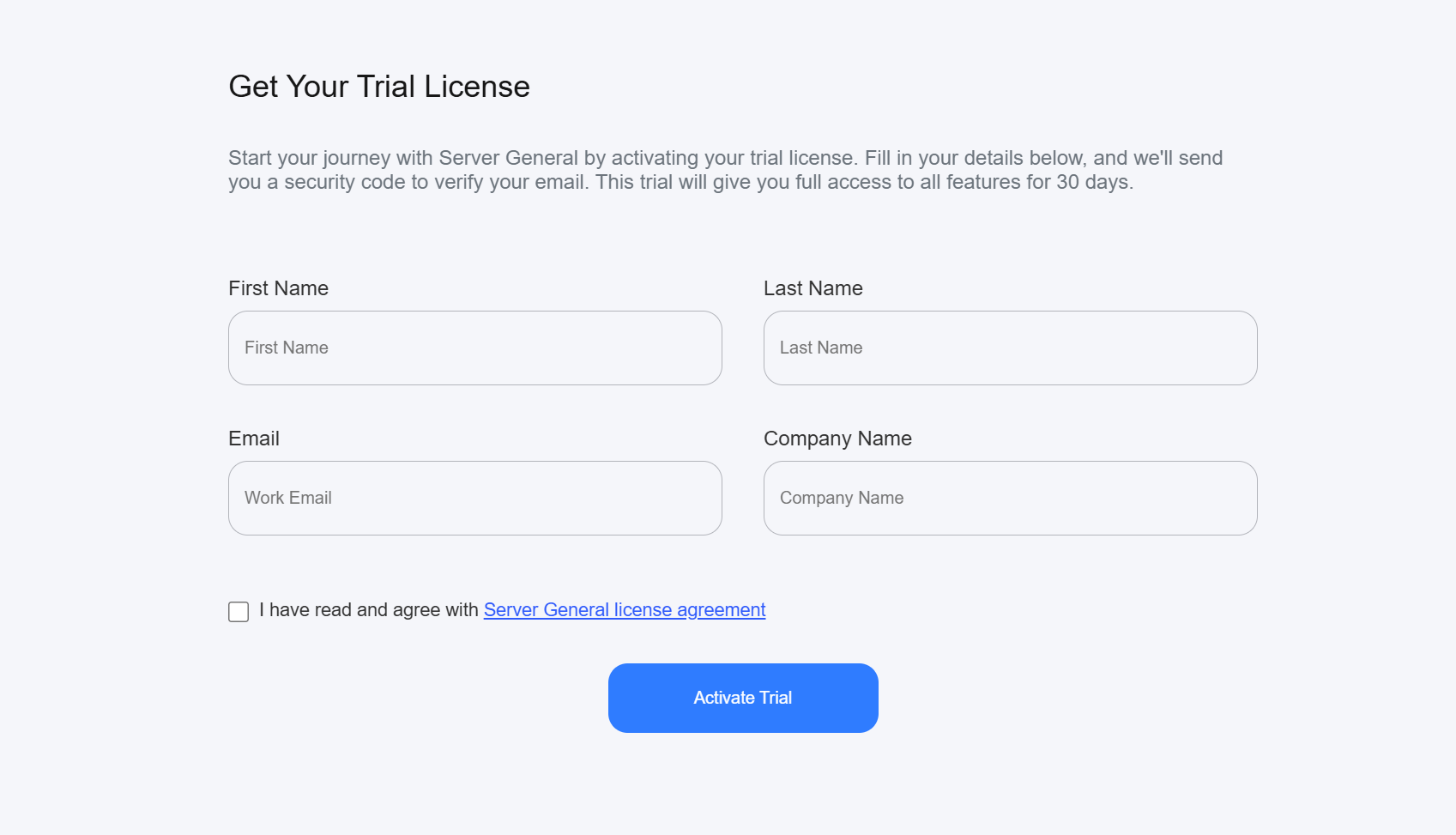
- If you didn't configure a license during installation:
- You will be prompted to obtain a "Trial License"
- Follow the on-screen instructions to get your trial license
Step 3: Security Configuration
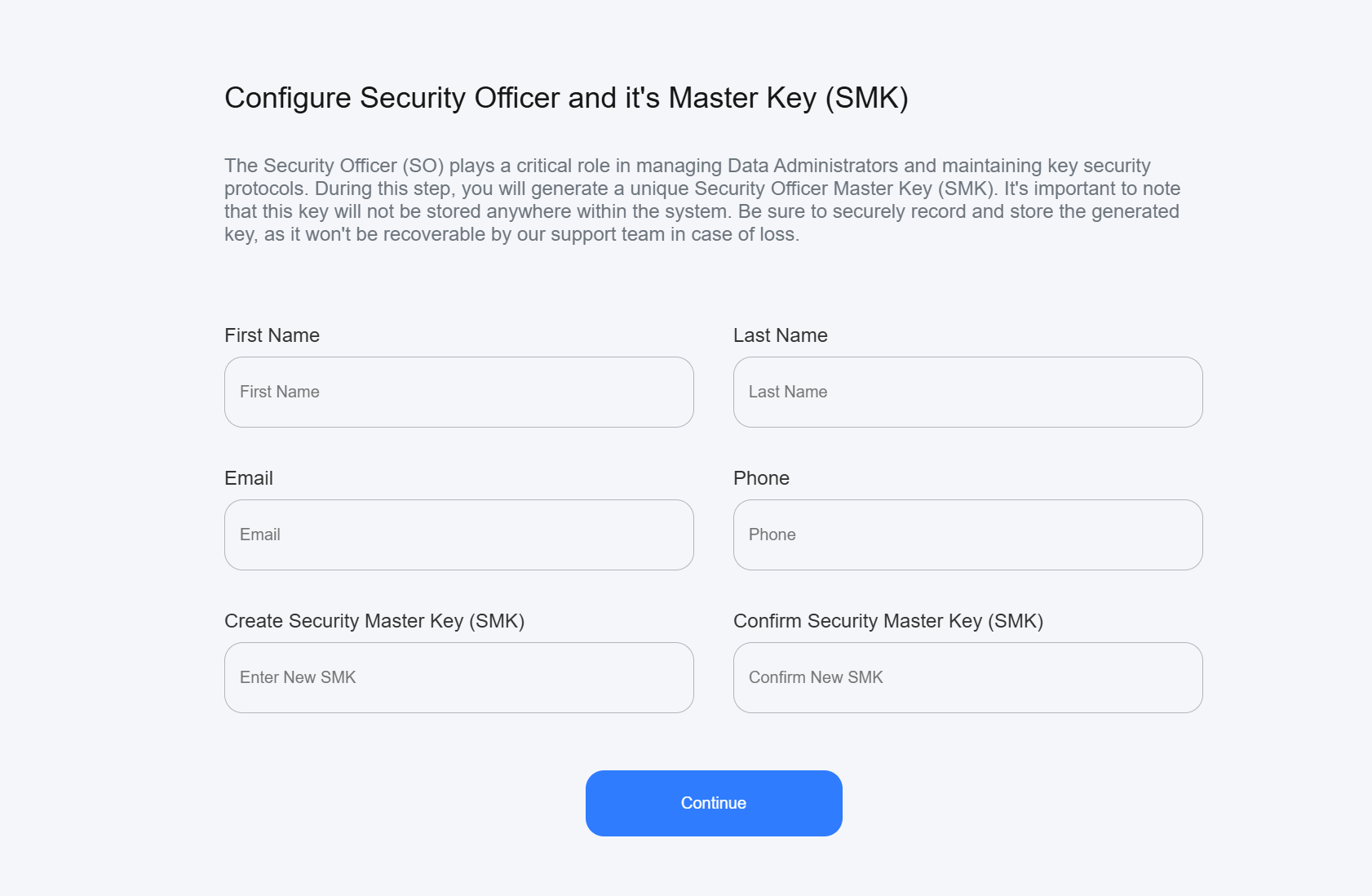
- Configure Security Officer (SO):
- Enter full name and contact information of the Security Officer
- Generate a secure Security Officer Master Key (SMK, minimum 16 characters)
- Store SMK safely - it cannot be recovered if lost
- This key authenticates the Security Officer who manages other administrators
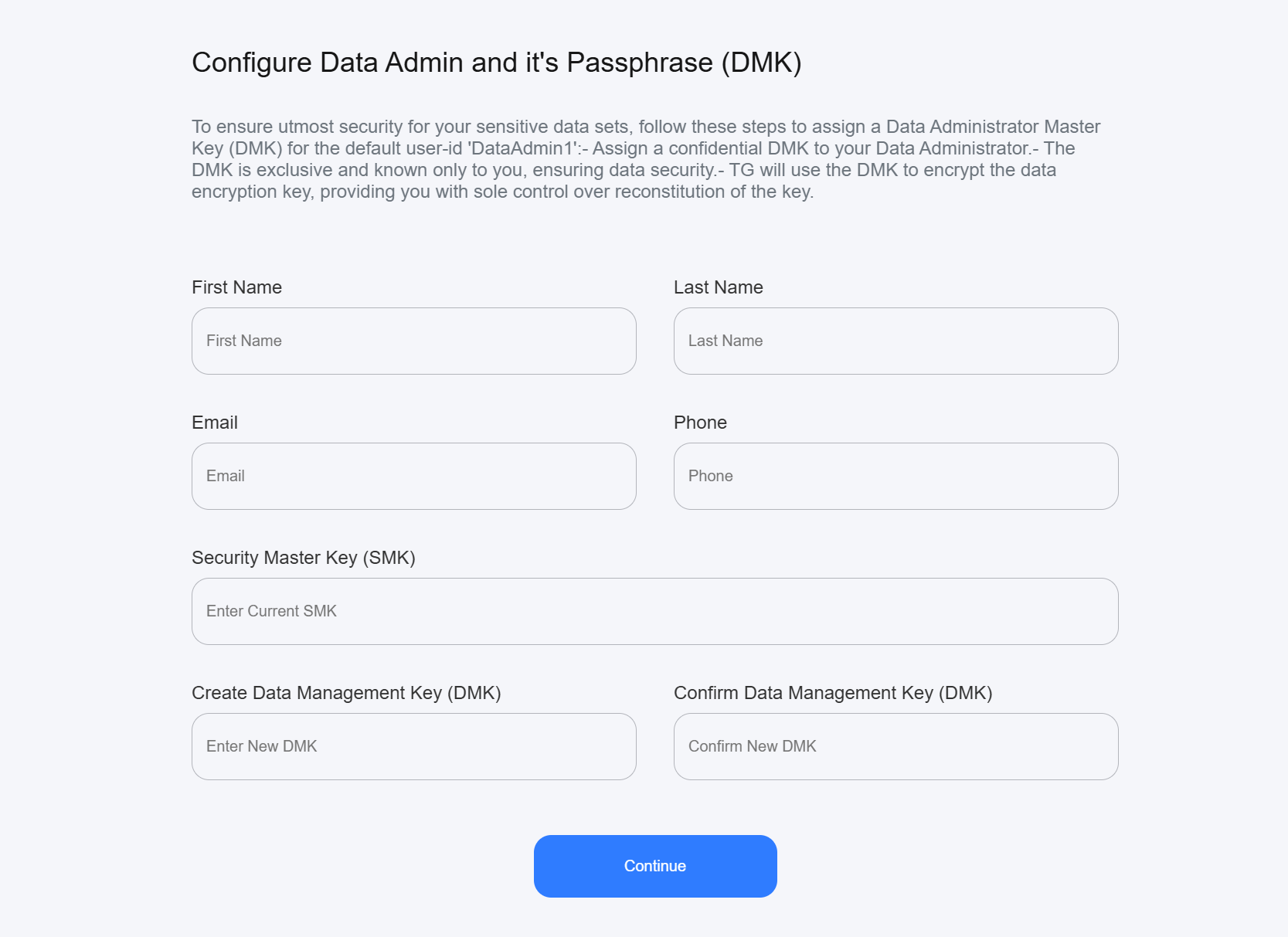
- Configure Data Administrator (DA):
- Enter full name and contact information of the Data Administrator
- Generate a secure Data Administrator Management Key (DMK)
- Store DMK safely - it cannot be recovered if lost
- This key authenticates the Data Administrator who manages sensitive data sets
- Upon successful configuration, you will be directed to the TG Console Dashboard
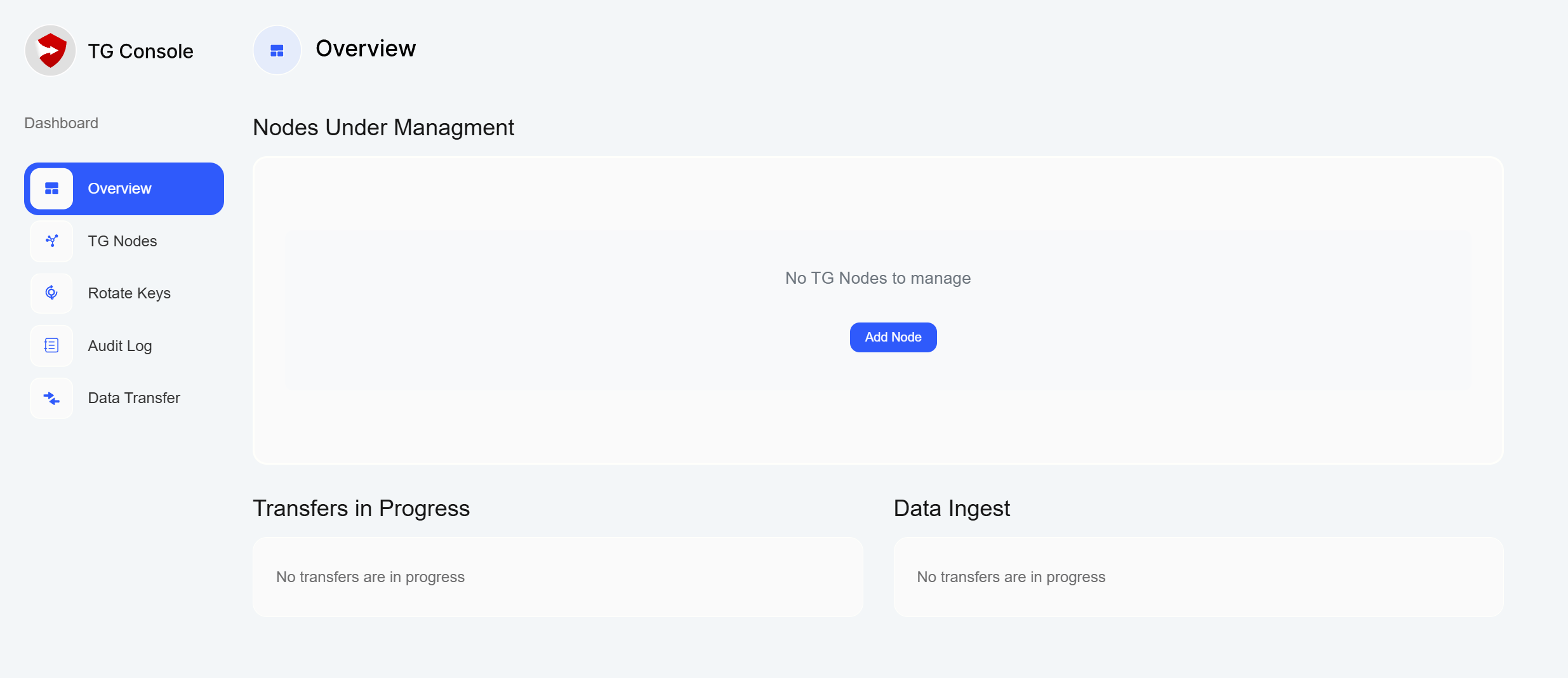
8. TG Node Deployment
After setting up TG Console, you'll need to deploy and configure your TG Nodes. Let's start with the source node.
Step 1: Node Preparation
- Deploy Ubuntu 22.04 on your chosen server
- Ensure network connectivity to TG Console
- Request a license key from https://www.servergeneral.com/get-license
Step 2: Node Installation
wget https://www.servergeneral.com/tg-installchmod +x tg-installsudo ./tg-install --tg-node <TG-Console IP> -l <license key>
The above will install and automatically register the TG Node with your TG Console instance.
Step 3: Node Configuration
- In TG Console, open "TG Nodes" page and click "+" button to add TG Node. Follow on-screen instructions
- Note the pre-configured secure directories:
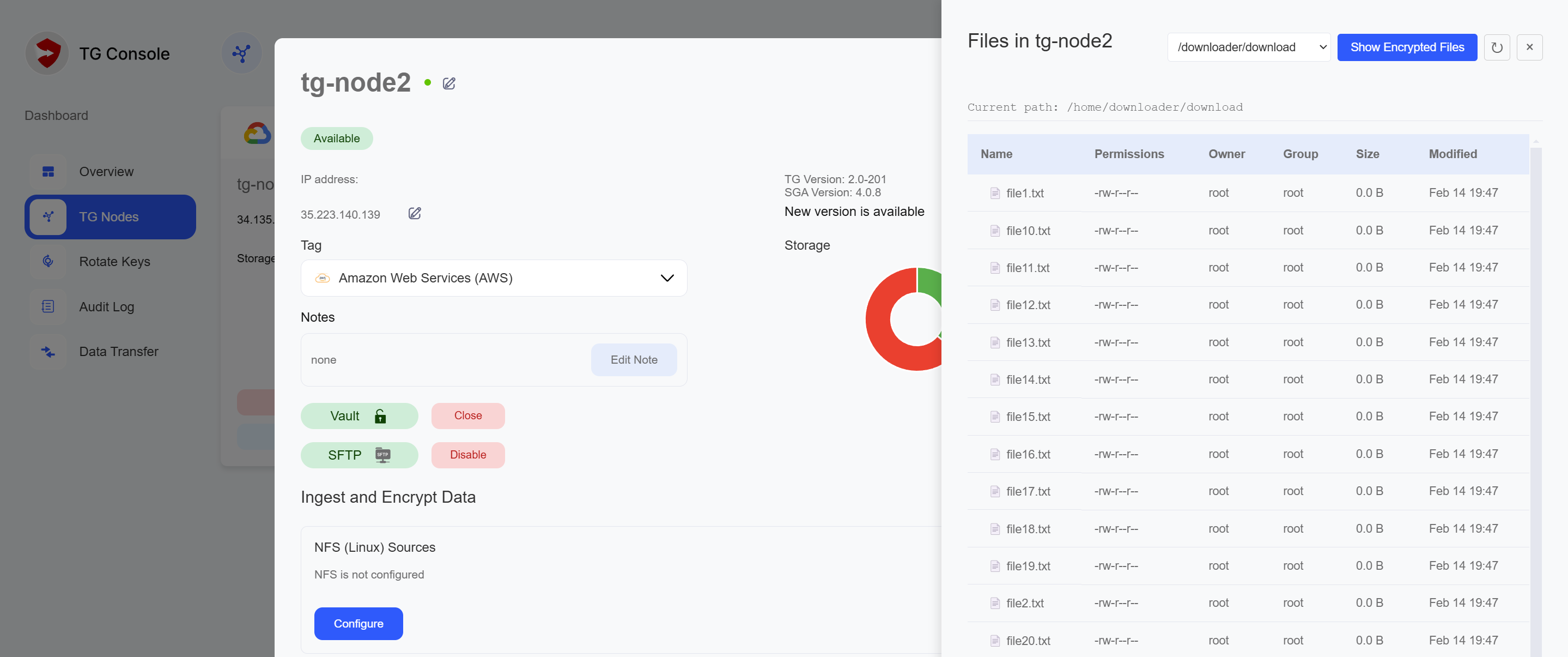
/home/uploader/upload- Place files here that you want to transfer to other nodes/home/downloader/download- Access files here that were received from other nodes
- Set up SFTP access
- Manage vault (open/close)
Repeat these steps for your destination node.
After finishing setup, you should see TG Nodes being available for management in TG Console UI:

9. Data Transfer Setup
Step 1: Preparing Source Node
- Open the source node's vault:
- Navigate to "TG Nodes"
- Select source node and click "Manage"
- Click "Open Vault"
- Enter DMK when prompted
- Upload data using SFTP:
- Click "Enable" next to the SFTP status indicator
- Enter DMK when prompted
- Save or copy the username and one time password for "uploader"
- Connect using your SFTP client
- Place files in
/home/uploader/uploaddirectory to prepare them for transfer - Ensure vault remains open during upload
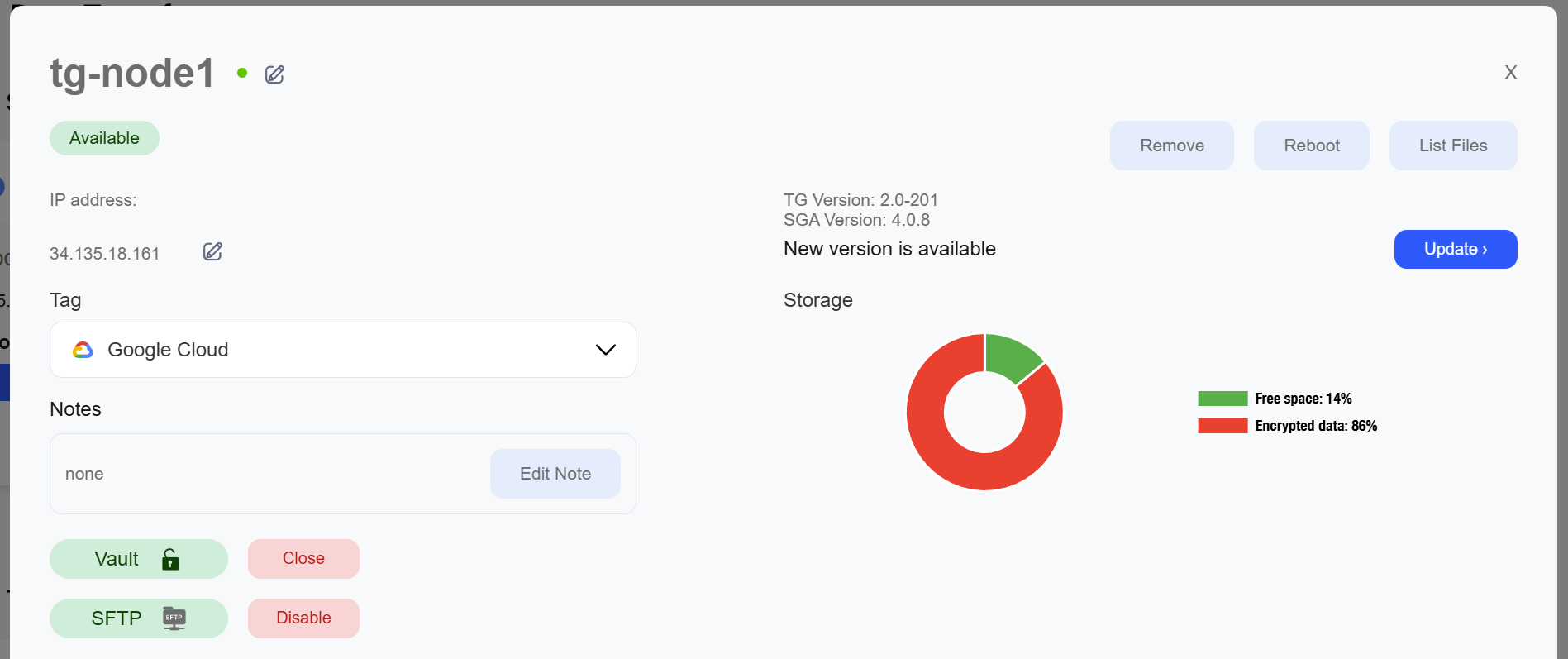
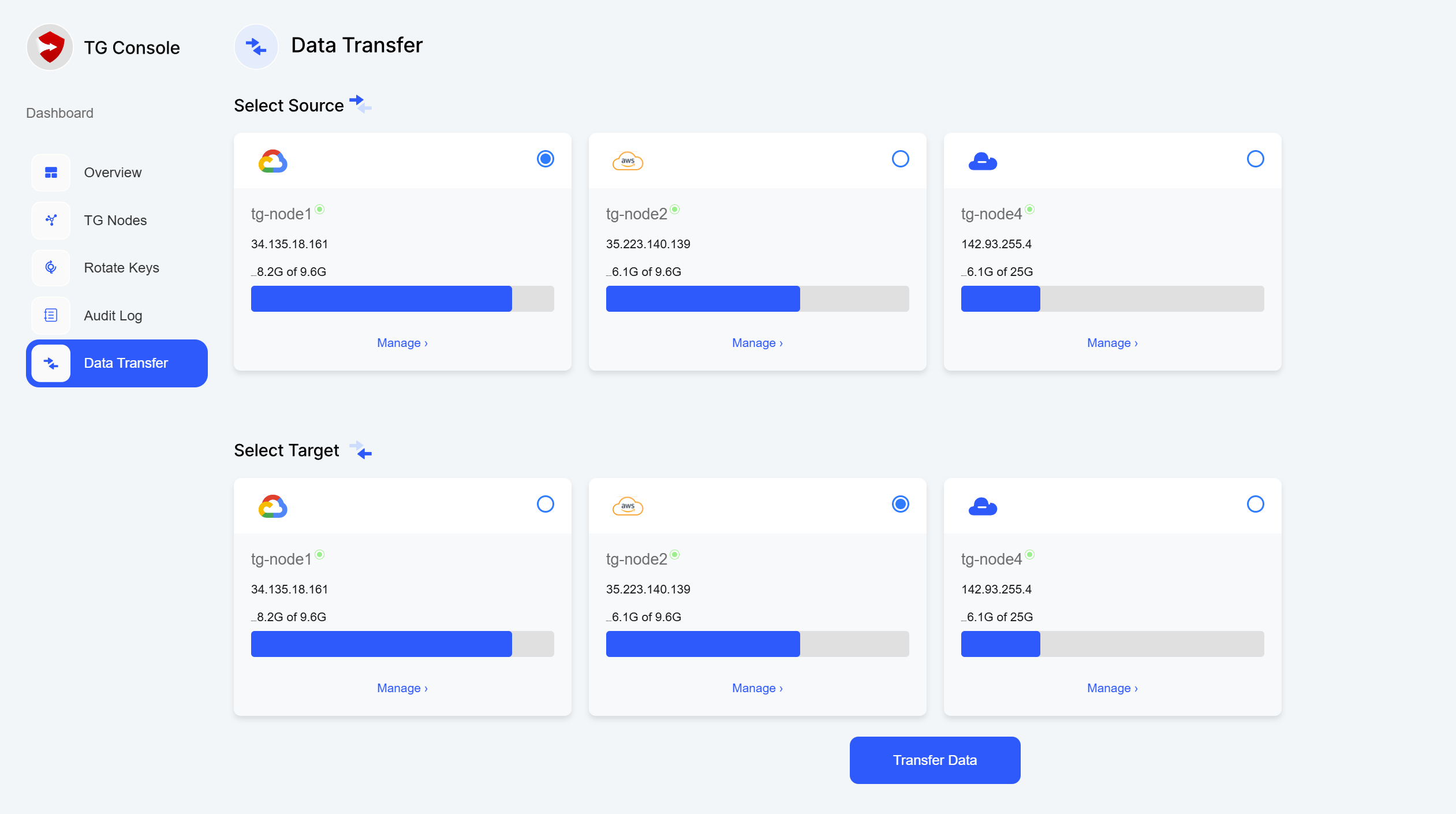
Step 2: Configuring Transfer
- In TG Console, navigate to "Data Transfer"
- Create new transfer job:
- Select source and destination nodes
- Click "Transfer Data"
- Enter DMK when prompted
- Review transfer settings
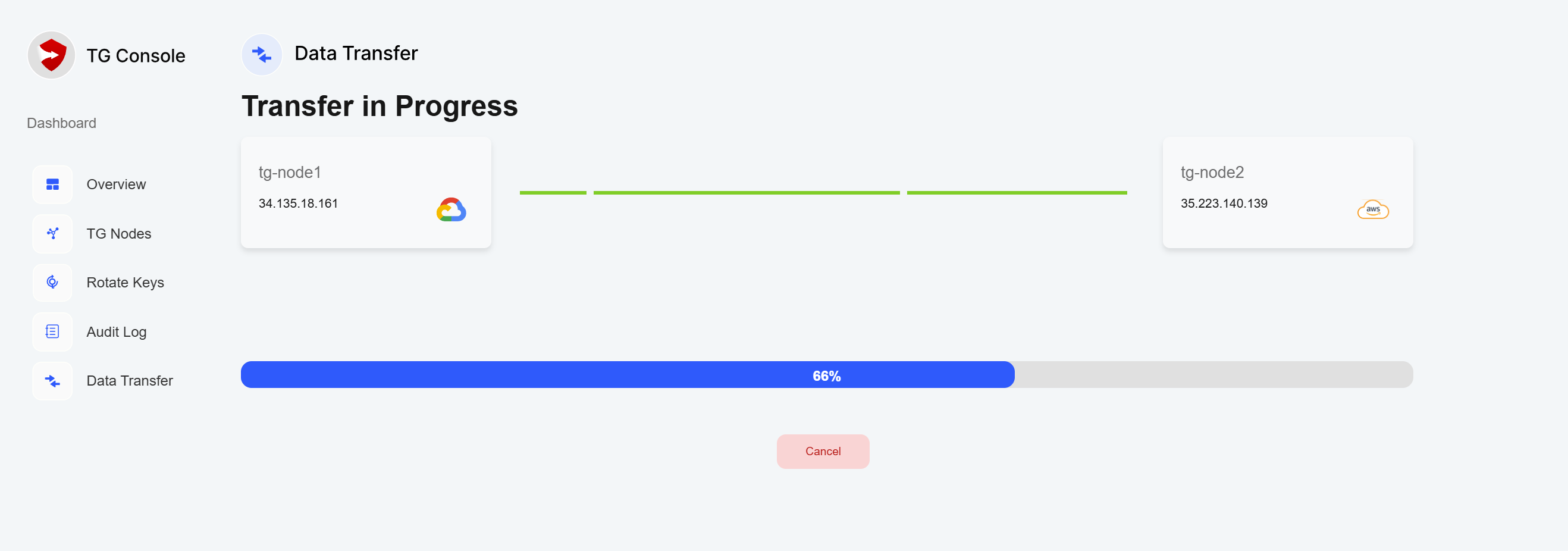
Step 3: Executing Transfer
- Initiate the transfer
- Monitor progress through TG Console
- Verify transfer completion
- Check transfer logs and reports
Step 4: Accessing Transferred Data
- Open the destination node's vault:
- Navigate to "TG Nodes"
- Select destination node and click "Manage"
- Click "Open Vault"
- Enter DMK when prompted
- Download data using SFTP:
- Click "Enable" next to the SFTP status indicator
- Enter DMK when prompted
- Save or copy the username and one time password for "downloader"
- Connect using your SFTP client
- Access files from
/home/downloader/downloaddirectory - Ensure vault remains open during download
- After completing the transfer:
- Verify data integrity
- Close the vault
For high-speed transfer evaluation or specific performance requirements, please contact your sales representative for additional configuration guidance.
10. Advanced Features
Monitoring and Reporting
TG Console provides comprehensive monitoring capabilities:
- Real-time Transfer Monitoring:
- Transfer progress and speeds
- Node status and health
- Vault states
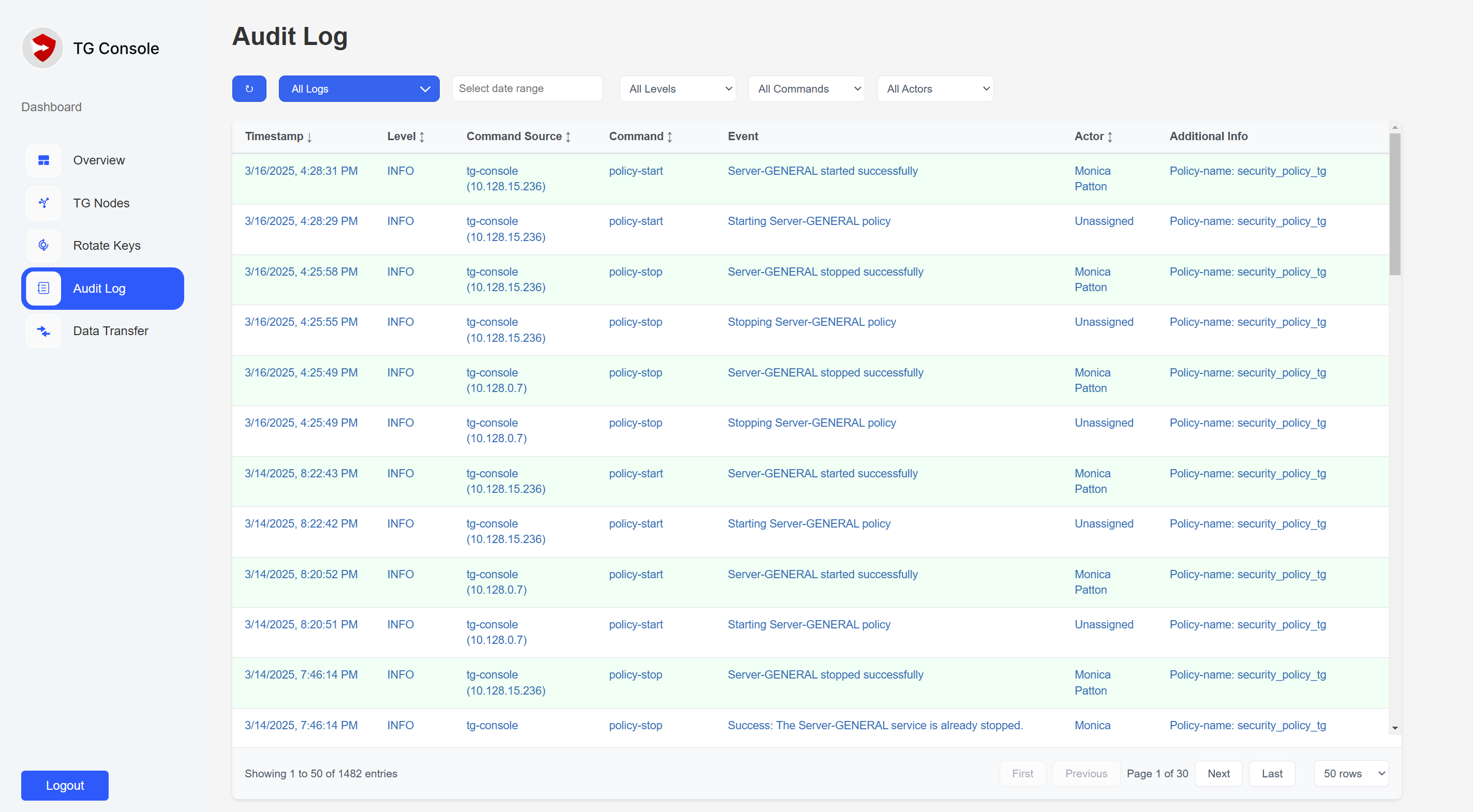
- Audit Logging:
- User actions and authentication
- Transfer operations
- System configuration changes
Security Features
- Key Rotation
- Access Control:
- Role-based permissions
- Session management
- Vault Management
11. Troubleshooting
Common scenarios and their solutions:
- Connection Issues:
- Verify network connectivity between components
- Check firewall rules
- Validate SSH configurations
- Transfer Failures:
- Check vault states
- Verify available disk space
- Review transfer logs
- Authentication Problems:
- Confirm correct credentials
- Verify key status
- Check role permissions
For additional support or specific configuration requirements, contact your Server General representative.
For high-speed transfer evaluation or specific performance requirements, please contact your sales representative for additional configuration guidance.